xctf WEB2 php解码
这是来自XCTF 攻防世界中的 web高级的一道题,某种意义上来说超级简单的
index.php 页面:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| <?php
$miwen="a1zLbgQsCESEIqRLwuQAyMwLyq2L5VwBxqGA3RQAyumZ0tmMvSGM2ZwB4tws";
function encode($str){
$_o=strrev($str);
for($_0=0;$_0<strlen($_o);$_0++){
$_c=substr($_o,$_0,1);
$__=ord($_c)+1;
$_c=chr($__);
$_=$_.$_c;
}
return str_rot13(strrev(base64_encode($_)));
}
highlight_file(__FILE__);
?>
|
按上思路编写解码的php文件:
exp.php:
1
2
3
4
5
6
7
8
9
10
11
12
13
| <?php
$str = "a1zLbgQsCESEIqRLwuQAyMwLyq2L5VwBxqGA3RQAyumZ0tmMvSGM2ZwB4tws";
$str = base64_decode(strrev(str_rot13($str)));
$_o = strrev($str);
for($_0=0;$_0<strlen($_o);$_0++){
$_c=substr($_o,$_0,1);
$__=ord($_c)-1;
$_c=chr($__);
$_=$_.$_c;
}
echo $_;
?>
|
取得flag:
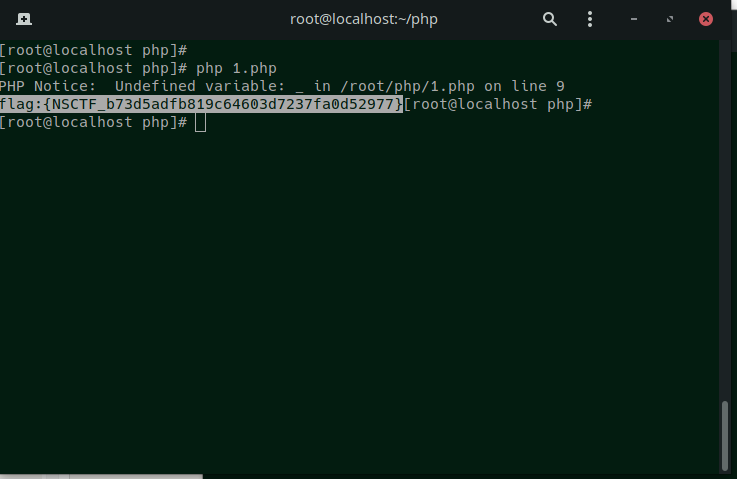
参考资料:
https://www.runoob.com/php/func-string-str-rot13.html
https://www.runoob.com/php/func-string-strrev.html
https://www.runoob.com/php/func-string-substr.html
